Commissioned by One Identity
1 Introduction
Digital transformation is no longer optional for businesses and organizations if they wish to stay competitive and deliver greater value to customers. But as they seek to embrace the advantages of Cloud, IoT, AI and Big Data projects across extended infrastructures, organizations need to be aware of the cyber security, compliance and identity risks that digital transformation also creates.
While these risks are serious, they can be significantly reduced through intelligent, fit for purpose and structured deployment of security solutions. As agile access and identity requests are a prime characteristic of a successful digital environment it follows that one of the most important tools to manage this securely is Privileged Access Management (PAM).
Privileged Access Management (PAM) solutions are critical cybersecurity controls that address the security risks associated with the use of privileged access in organizations and companies. Traditionally, there are primarily two types of privileged users:
- Privileged Business Users - those who need access to sensitive data and information assets such as HR records, payroll details, financial information or intellectual property, and social media accounts.
- Privileged IT Users – those who need access to the IT infrastructure supporting the business. Such permissions are usually granted to IT admins who need access to system accounts, software accounts or operational accounts.
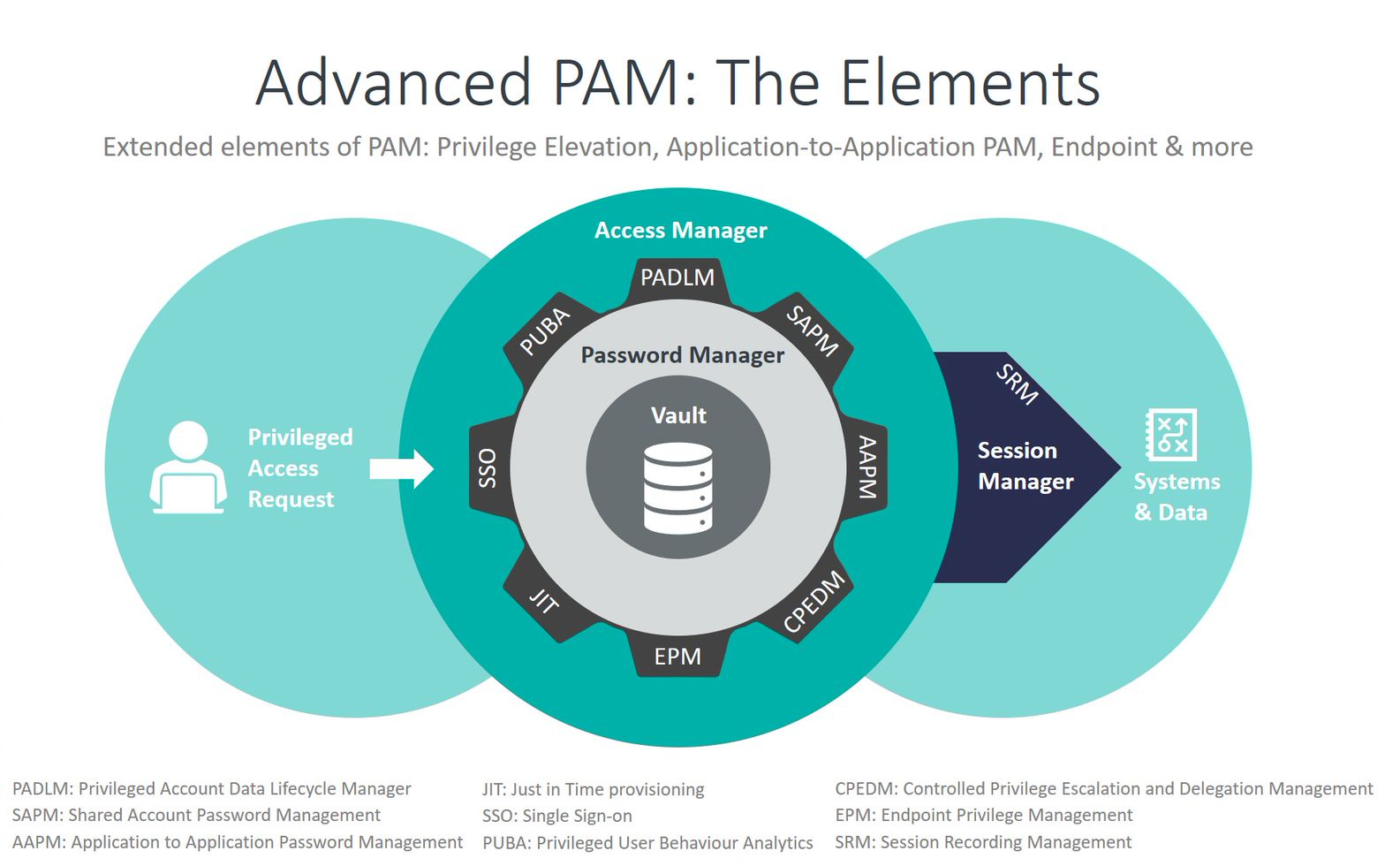
Among the key challenges that drive the need for privilege management are:
- Abuse of shared credentials
- Abuse of elevated privileges by unauthorized users
- Hijacking of privileged credentials by cyber-criminals
- Abuse of privileges on third-party systems
- Accidental misuse of elevated privileges by users
- The requirement to perform attestations on privileged users and admin accounts
Furthermore, there are several other operational, governance and regulatory requirements associated with privileged access:
- Discovery of shared accounts, software and service accounts across the IT infrastructure
- Identifying and tracking of ownership of privileged accounts throughout their lifecycle
- Establishing Single Sign-on sessions to target systems for better operational efficiency of administrators
- Auditing, recording and monitoring of privileged activities for regulatory compliance
- Managing, restricting, and monitoring administrative access of IT outsourcing vendors and MSPs to internal IT systems
- Managing, restricting, and monitoring administrative access of internal users to cloud services
In recent years, PAM solutions have become more sophisticated making them robust security management tools. While credential vaulting, password rotation, privilege delegation and activity monitoring are now more common, more advanced capabilities such as privileged user analytics, risk-based session monitoring, advanced threat protection, and the ability to embrace PAM into an enterprise governance program are the new standard to protect against today’s threats in complex environments.










































