1 Executive Summary
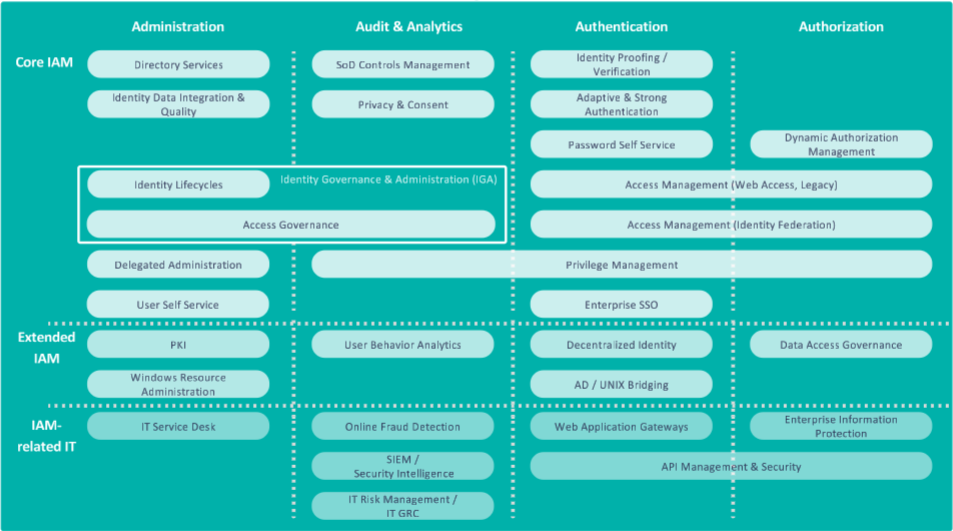
Digital identities are at the heart of Digital Transformation, Information Security and Privacy Therefore it has never been more important for enterprises to have the capability to manage identities effectively in a rapidly changing business, regulatory and IT environment to ensure they remain competitive, compliant and secure. As a result, many organizations are reviewing their Identity Governance & Administration (IGA) capability that covers these core areas within the wider Identity & Access Management (IAM) architecture. However, business cases for new IGA projects may be difficult to make because of past project failures and the resultant reticence of the business to invest further. This Leadership Brief outlines the biggest risks and pitfalls, such as poor business alignment, lack of necessary skills, poor product and deployment choices, and inadequate architectures. The recommendations section provides suggestions for avoiding or mitigating these risks with tactical, strategic, technical, organizational, and project-focused measures.