1 Recommendations
IAM is the granddaddy of identity related technologies, having been with us since the last century. But in that time, a mythology has been created including things that were once true but are no longer, things that are only partially true and things which never did have any validity. These are our recommendations for overcoming these myths.
- Integrated architecture, services, applications and – equally as important – user education are necessary. No software alone can solve your IAM problems.
- Dynamic, policy-based access control is necessary to protect your data and resources; static ACLs (Access Control Lists) no longer do the job properly.
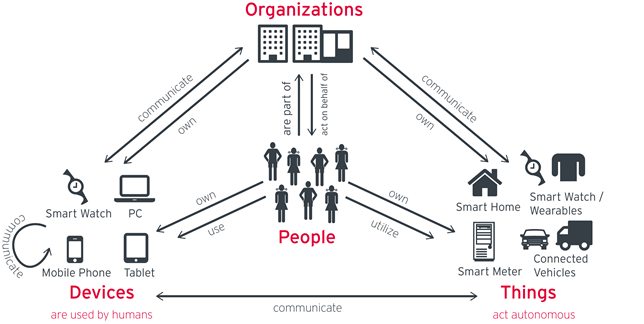
- Proper IAM, as well as proper governance, requires all users and resources are part of a single integrated identity domain – separate structures for on-premise business, industrial control systems and cloud-based services can only stay separate at the risk of massive data breaches.
- Authentication methods all have exploitable flaws. Use risk mitigation techniques and policies to overcome their weaknesses. None of these methods is a “magic bullet.”
- Employee education –especially in the area of IAM – must be an on-going process. To say that “they all attended an orientation briefing and signed the appropriate policy when they joined“ ignores the lesser fact that not everyone retains information from orientation and the greater fact that not everyone (e.g., partners, vendors, contractors) goes through orientation.










































