1 Introduction
This report is an overview of the market for Privilege Access Management (PAM) solutions and provides a compass to help buyers find the solution that best meets their needs. KuppingerCole examines the market segment, vendor functionality, relative market share, and innovative approaches to providing PAM for DevOps solutions. This follow up to the larger Leadership Compass PAM 2020 (published May 2020) concentrates on those vendors we believe are best addressing the challenge of managing PAM within DevOps environments. Many vendors have yet to consider DevOps and agile environments, or believe their solutions cover this adequately, hence a smaller report.
However, the view of KuppingerCole is that the 10 vendors featured are currently doing most for DevOps by adding special technologies and capabilities that address the operating environments and pressures that DevOps teams tend to work in.
1.1 Market segment
Privileged Access Management (PAM) solutions are critical cybersecurity controls that address the security risks associated with the use of privileged access in organizations and companies. Traditionally, there have been primarily two types of privileged users.
Privileged IT users are those who need access to the IT infrastructure supporting the business. Such permissions are usually granted to IT admins who need access to system accounts, software accounts or operational accounts.
There are now also privileged business users, those who need access to sensitive data and information assets such as HR records, payroll details, financial information or intellectual property, and social media accounts.
The picture has become more complicated with many more of these non-traditional users requiring and getting privileged access to IT tools and business data. Some will be employees working on special projects, others may be developers building applications or third-party contractual workers. With the onset of digital transformation, organizations have seen the number of privileged users multiply as new types of operations such as DevOps have needed access to privileged accounts. Such are the critical demands of DevOps that several PAM vendors are now adding specific capabilities to address them.
In recent years, Privileged Access Management (PAM) has become one of the fastest growing areas of cyber security and risk management solutions. KuppingerCole estimates that the number of major vendors in the space is around 40 with a combined annual revenue of around $2.2bn per annum, predicted to grow to $5.4bn by 2025 (see Figure 1).
That growth has largely been driven by changes in business computing practices and compliance demands from governments and trading bodies, as well as increased levels of cybercrime. The growth of Advanced Persistent Threats (APT) and the ability of hackers to access service accounts is a threat PAM can help with. Protecting admin and service accounts can make it more difficult for state actors and corporate espionage agents to abscond with data. PAM controls create additional hurdles for would-be attackers to pass as well as potentially more indicators of compromise (IoC) and thus opportunities for being discovered earlier in the process.
Digital transformation, regulations such as GDPR, the shift to the cloud and, most recently, the growth of DevOps in organizations looking to accelerate their application development processes are all adding to the growth.
The reason for this mini boom is that these trends have triggered an explosion in data and services designated as business critical or confidential, and a concurrent rise in the number of users and applications that need to access them. IT administrators realised that without dedicated solutions to manage all these, the organizations would be at great risk of hacks and security breaches. Hackers and cyber criminals have long targeted unprotected privileged accounts as one of the easiest routes to get inside an organization.
In recent years, PAM solutions have become more sophisticated, making them robust security management tools in themselves. While credential vaulting, password rotation, controlled elevation and delegation of privileges, session establishment and activity monitoring are now almost standard features, more advanced capabilities such as privileged user analytics, risk-based session monitoring, advanced threat protection, and the ability to embrace PAM scenarios in an enterprise governance program are becoming the new standard to protect against today’s threats. Many vendors are integrating these features into comprehensive PAM suites while a new generation of providers are targeting niche areas of Privileged Access Management. Overall, it is one of the more dynamic and interesting parts of security and access management.

1.1.1 The impact of agile development and DevOps on PAM
The pressure on organizations to develop their IT infrastructures within an automated Continuous Integration and Delivery framework (CI/CD) is increasing. The directive is from senior management who wish to see improvements in competitiveness through IT, and IT team leaders looking for boosts in software productivity and efficiency to meet the demands of senior management. Modern organizations are an unwieldy mixture of interconnected code and applications including microservices, APIs, desktop apps and mobile apps and to keep all these up to speed requires a constant stream of updates and patches – not to mention the roll out of brand-new software projects. It is not uncommon today for applications to be updated many times a day.
Today, the CI/CD trend impacts as much on third party and customer facing, software driven products as it does on internal IT projects. In a world seeking perfection, nothing is ever finished. At the heart of this process is the DevOps IT team culture which emerged to break down the traditional engineering and operations silos that existed previously, and often stalled software development, and introduced errors. It was found that co-operation between the teams and the breakdown of traditional IT roles helped facilitate the desired CI/CD framework as developers became used to agile turnaround and rapid software delivery times.
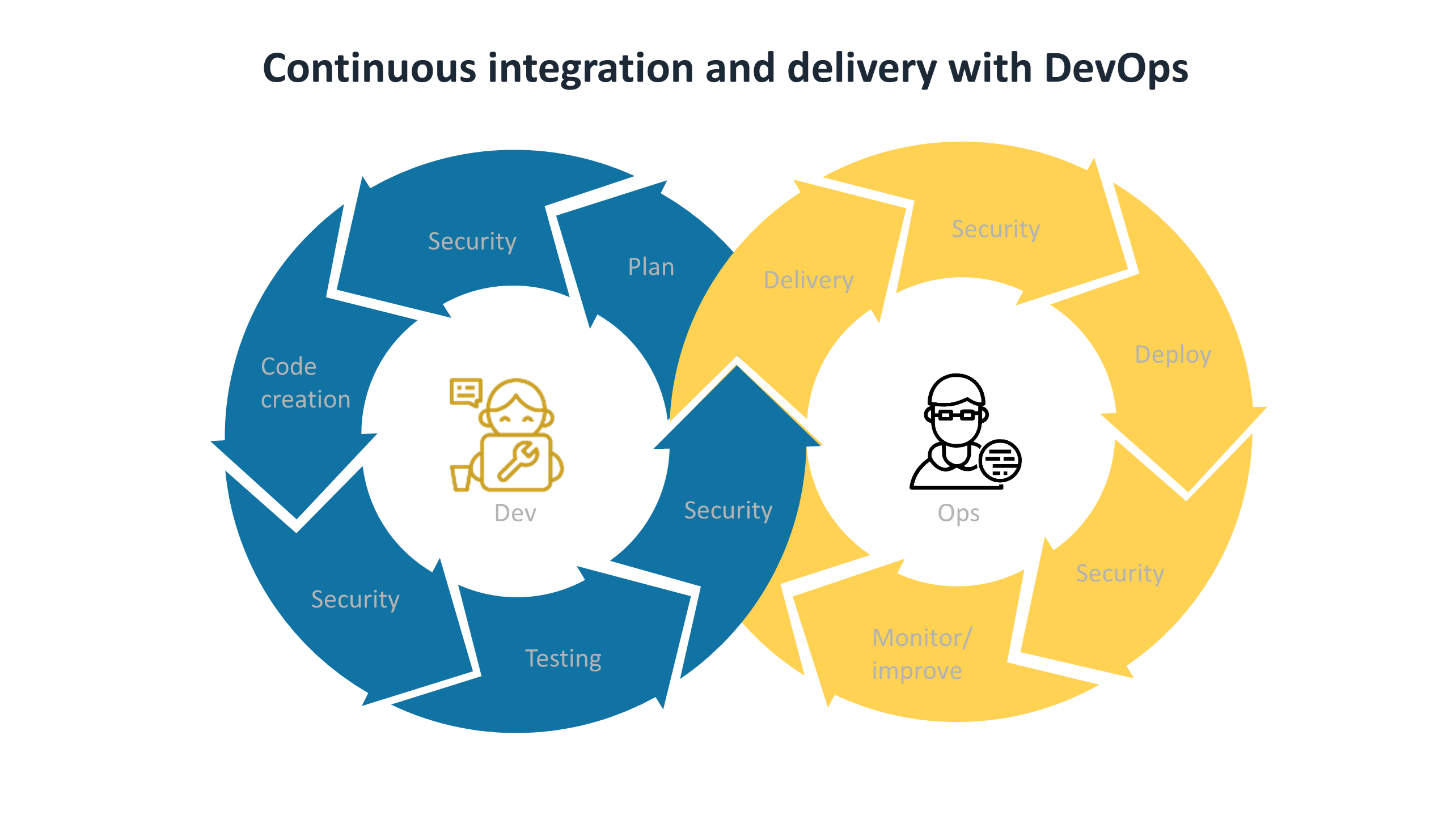
Transparent Security platforms including PAM must be embedded within the CI/CD lifecycle that DevOps teams work within. A security feedback mechanism is also advisable to allow DevOps and other agile development teams to act quickly on vulnerabilities as they arise.
1.1.2 Why DevOps is now critical to managing privileged accounts in organizations
Those working in DevOps store, compile and test code that will involve privileged access to specific data sources, tools, applications and other resources that are classified as confidential, and must be kept secure. Today, this will include individual pieces of code, containers, and APIs as well as discrete data that relates to company projects or individuals.
DevOps will access and process privileged data and entities on a continuous basis. Without a platform to monitor, record and control this access, countless vulnerabilities will be introduced every day. For example, developers committed to their job, will often perform actions that make their operations quicker but introduce security risks. They may locally store or share credentials to privileged tools and data or embed them within an application or container they are working with. Developers may share passwords and code, and admins may allow privilege to users on an ad hoc bases – a process known as privilege creep.
The challenge is finding a PAM solution that can work at the pressure and speed that DevOps already work to and keep all secrets secure. It must not get in the way - it must be secure and accountable through integrated tools or via third-party integrations. In this Leadership Compass we assess those PAM vendors that are addressing the needs of DevOps and agile environments. Some are offering DevOps capabilities as an add-on to existing suites, while others offer specific authentication toolsets that work well with providing privileged access to DevOps teams and non-human users. Currently vendors offer traditional vaults or certificates to authenticate users within the DevOps environment (see Figure 3).










































