1 Introduction
eCommerce businesses and other organizations that interact directly with end-users over the web are increasingly looking for better solutions for authenticating those users. Password authentication is not only insecure, but it leads to poor consumer experiences and is costly for businesses to maintain. Knowledge-based authentication is an even worse alternative. In order to deter fraud, comply with new regional and industry-specific regulations, and improve the customer experience, organizations are adopting Consumer Identity and Access Management (CIAM) solutions or enhancing their existing customer-facing IAM solutions with modular authentication services.
Most organizations have IAM products in place already. However, many are finding that their current solutions are not able to meet consumer expectations or security requirements.
There are a number of motivations driving businesses to enhance their authentication solutions:
- Improve consumer experiences
- Increase security
- Reduce fraud
- Preserve privacy
- Comply with regulations requiring strong or multi-factor authentication, such as AML (Anti-Money Laundering), EU PSD2, KYC (Know Your Customer), and NY CCR (New York cybersecurity law)
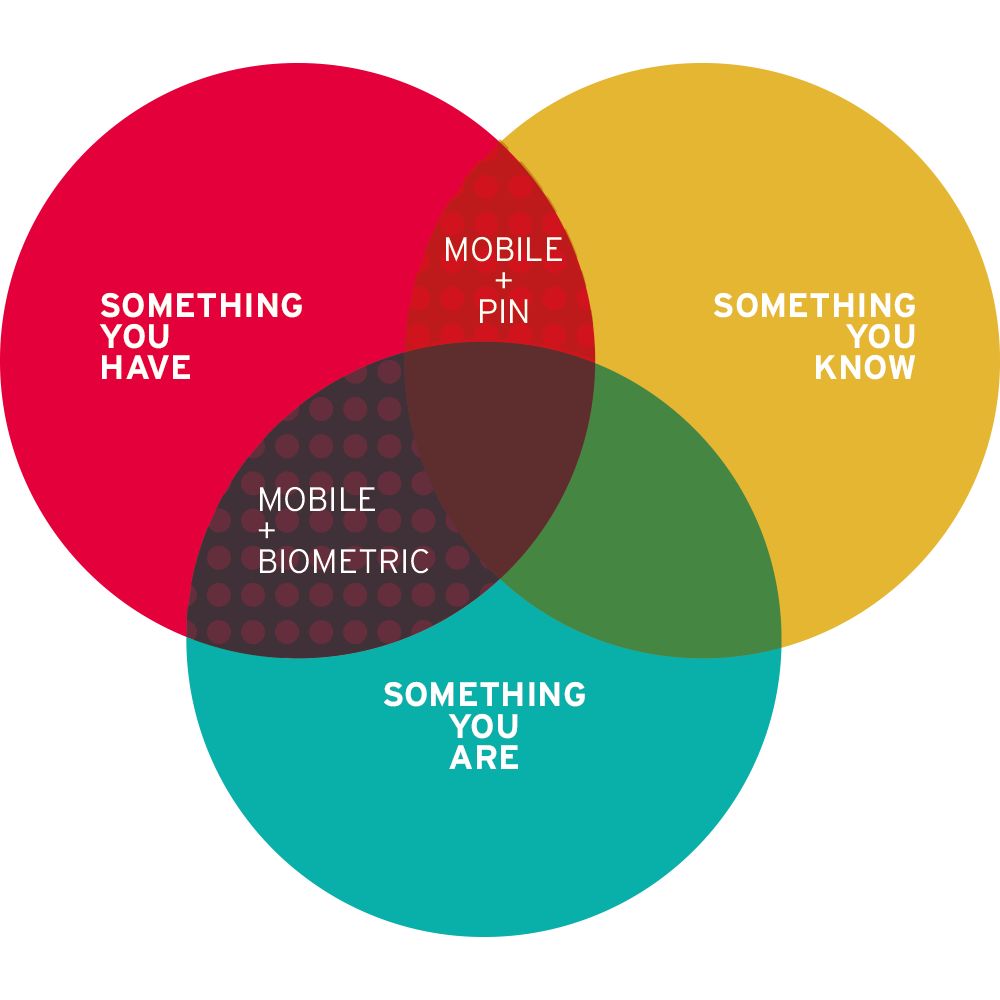
Consumer authentication services today are primarily leveraging mobile devices, particularly smartphones. Given the near ubiquity of these devices, it’s not a surprise. Smartphones can serve as a second factor, or the “something you have” factor in Multi-Factor Authentication (MFA) scenarios.
This KuppingerCole Leadership Compass provides an overview of the leading vendors in this market segment. Picking solutions always requires a thorough analysis of customer requirements and a comparison with product features. Leadership does not always mean that a product is the best fit for a customer and his requirements. However, this Leadership Compass will help identify those vendors that customers should look at more closely.
1.1 Market Segment
The Consumer Authentication market is growing, with some vendors offering mature solutions providing standard and deluxe features to support millions of users across every industrial sector. As will be reflected in this report, the solutions in this space are quite diverse. Some vendors have about every feature one could want in a consumer authentication service, while others are more specialized, and thus have different kinds of technical capabilities. For example, some smaller vendors are targeting the government-to-citizen (G2C) market as well as business-to-consumer (B2C). We sometimes see support for national e-IDs, x.509 certificates, and higher assurance authentication mechanisms in these vendors’ products compared to the rest.
Furthermore, KuppingerCole research indicates that the particular market segments that vendors choose to target often has a direct effect on the type of features available in their consumer authentication solutions. Consumer authentication product or service vendors that are primarily pursuing retail and media companies as clients tend to not have the customer-driven pressure to support high assurance authentication and complex attribute-based access controls. This Leadership Compass will examine solutions that are available for both on-premise and cloud-based deployment.
Many vendors are taking an “API-first” approach to consumer authentication, which allows organizations with in-house expertise to extend their existing IAM infrastructure to accommodate consumer use cases better. The API-first approach also permits in-house developers to easily “bolt-on” authentication services to existing or legacy Line of Business applications, without necessarily investing in a full-size CIAM solution. Identity API platforms are not always completely assembled products and services. Rather, these platforms are collections of tools, code, and templates. Identity API platforms may contain many open source elements, and generally leverage well-known standards. KuppingerCole is also producing a Leadership Compass focuses on Identity API platforms.











































