1 Introduction
Identity Governance and Administration (IGA), often referred to as integrated identity provisioning and access governance markets concerns the IAM capabilities that broadly deal with end-to-end identity life-cycle management, access entitlements, workflow and policy management, role management, access certification, SOD risk analysis, reporting as well as access intelligence. As IGA becomes an important security risk and management discipline directly impacting the security posture of any organization, a lack of basic IGA capabilities can leave organizations exposed to risks originating from inefficient administration of identities and access entitlements, poor role management and lack of adequate auditing and reporting. These risks range from identity thefts to unapproved and unauthorized changes, access creep, role bloating, delays in access fulfilment, orphan roles and accounts, SOD conflicts leading to occupational and other internal frauds. Several incidents in recent past have emphasized the need to have better IGA controls for organizations of all sizes, across all industry verticals.
Identity Governance and Administration (IGA) products support the consolidation of identity information across multiple repositories and systems of record such as HR and ERP systems in an organization’s IT environment. The identity information including user accounts, associated access entitlements and other identity attributes are collected from across the connected target systems for correlation and management of individual identities and user groups as well as roles through a centralized administration console.
The IGA products are primarily aimed at supporting the following activities in an organization:
- Automated provisioning and de-provisioning of user accounts across nominated target systems
- Synchronization of identity attributes and access entitlements related to user accounts and groups across the identity repositories
- Management of access entitlements and associated roles of users across the IT environment
- Configuration and enforcement of static as well as event-driven access policies for the accounts to access the IT systems and applications
- Allowing users to validate their access to systems and applications, reset the passwords and create new access requests using self-service options
- Verification and synchronization of user account passwords and other identity attributes from an authorized event and source across the identity repositories
- Reconciliation of access across the IT environment based on defined policies to ensure compliance and prevent SOD and other policy violations
- Supporting on-demand and event-driven user access certification campaigns to detect and mitigate access violations
- Auditing and reporting of access activities leading to critical information regarding service monitoring and optimization
The IGA market has witnessed several trends over the last few years including a major shift in the product strategy and development roadmaps to provide in-built support for cloud applications. These advancements to support the cloud integrations are majorly driven in two directions:
- IGA vendors that have re-architected their products to offer an identity bridging capability to integrate with cloud providers using industry specifications. Some IGA vendors have partnered with speciality identity brokers to extend on-premises IGA capabilities to cloud applications. Such approaches are suitable for organizations with a decent on-premises IT footprint and requirements to support complex IGA scenarios for legacy on-premises applications.
- IGA vendors that now offer a cloud IGA product that is cloud deployable with ready integrations with popular cloud applications as well as with standard on-premises applications. This approach is more suitable for organizations with a massive strategic focus on the move to cloud and looking at achieving the benefits of cloud IGA deployments such as shorter deployment cycles, faster upgrades and lower TCO in short term.
At KuppingerCole, we identify and group the core capabilities delivered by the IGA vendors primarily in two product categories: Identity Provisioning and Access Governance. The core capabilities within each of these groups are represented in the figure below:
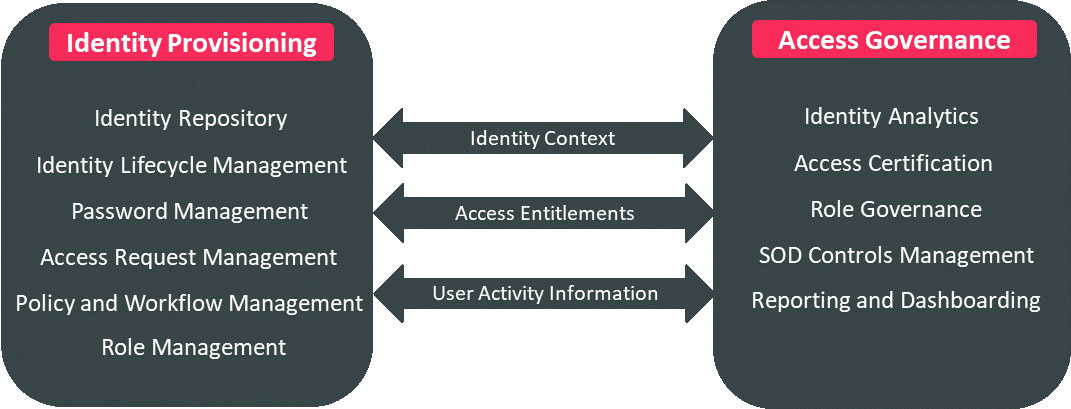
Besides these core functionalities, there are additional operational aspects that are considered to be important evaluating criteria for an IGA product or service and basically include capabilities such as UX (user experience), multi-tenancy, support for automation, high availability, ease of deployment, scalability and performance.
Please refer to Leadership Compass for Identity Governance and Administration for more details on the IGA capabilities discussed here.










































