1 Management Summary
If it is the goal of information security to enable the business as well as protect it, then the traditional network model of an insecure outside (the Internet) with a firewall protecting the secure internal network fails the business on both counts.
This old model is being actively bypassed by exploits from adversaries who want to steal information, extort money or damage the business operation, while simultaneously hindering business agility with a rigid border that must be traversed every time the organisation needs to interact outside their “hardened shell”.
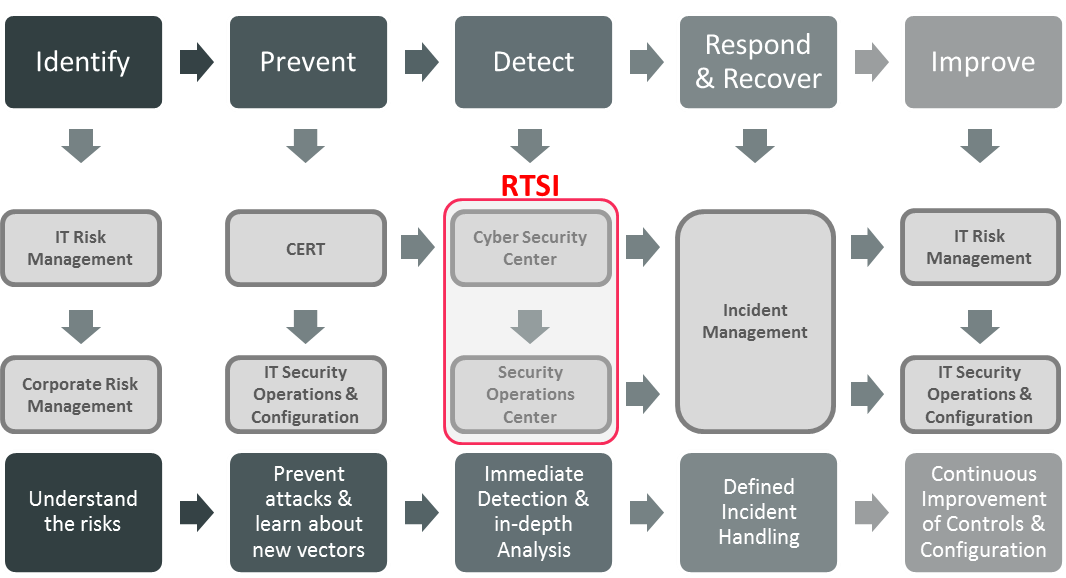
Instead we need to re-purpose the firewall, moving from one perimeter to many micro-perimeters, using one tool to centrally provide a consistent view of the configuration and the logs. Coupling this with analytic and real-time security intelligence (RTSI) should provide businesses with a greater level of protection from today’s threats.
This strategic approach should be driven by a good understanding of where the organisation’s data needs to flow, together with a set of modern appliances that place the protection and access as close as possible to the data the business defines as needing protecting.
This advisory note provides a broad set of high-level recommendations and approaches for aligning a modern network security architecture and security strategy with the needs of the business; resulting in an agile approach that enables data to flow to wherever and whoever is authorised to access it, as well as providing actionable advice for security organizations on how to:
- Understand the limitations of traditional firewall and network architecture
- The need to perform a network data flow analysis
- Use this understanding to drive a network and security strategy
- Adopt a “data-centric” security model, moving the security and protection of data closer to the data itself
- Make the concept of “inside” and “outside” irrelevant, protecting data to the same level wherever it, or the device it resides on, happens to be
- Leverage identity to provide frictionless access to data and systems
- Ensure that firewall and other logs are coupled with the analytics and threat intelligence strategy











































